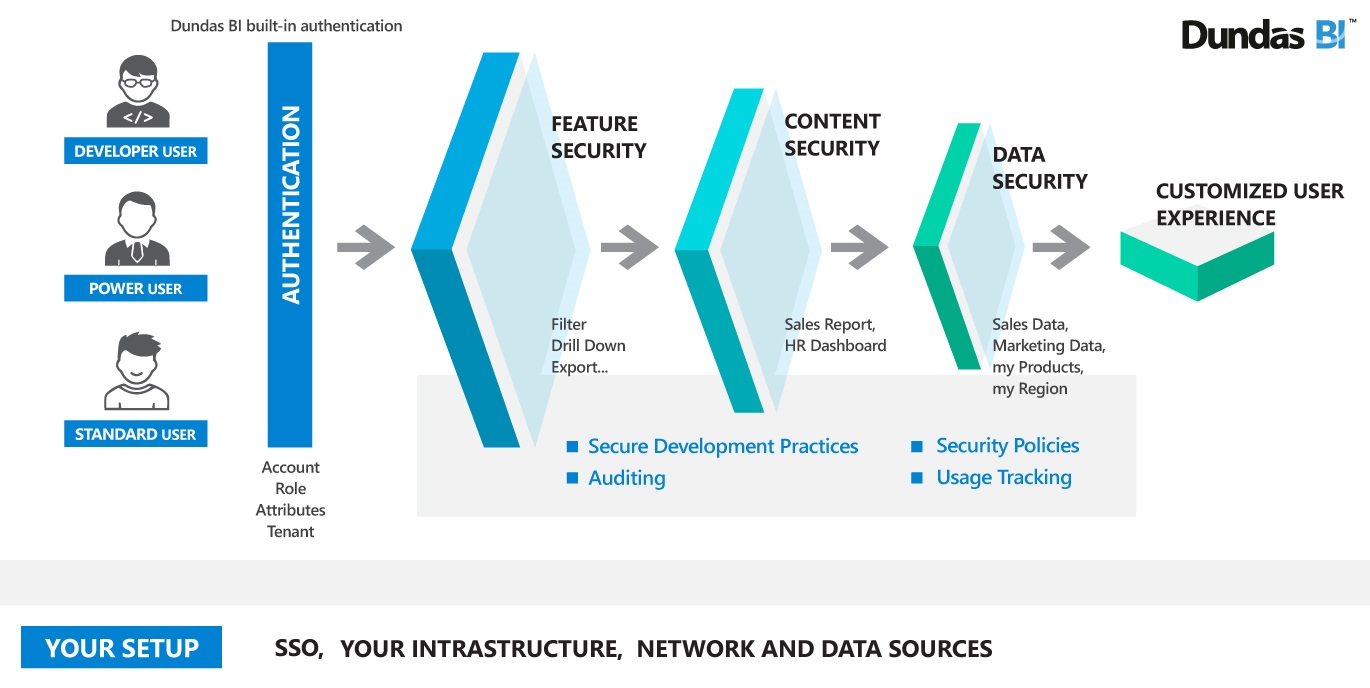
Security overview
1. Overview
There are a wide variety of security and permissions options you can use to customize and secure your deployment. You can customize access to functionality and content at both broad and granular levels, set up row-level security or other data access control, monitor application usage and events, and integrate with your own organization's security infrastructure.
2. Seat types
Each user is assigned a seat type, which determines which areas of the application they can access if not restricted by privileges described in later sections. For example:
- Standard Users and above (all users) can create and interact with views such as dashboards, reports, and slideshows to combine visualizations together, filter, drill down, etc.
- Power Users and above can create and edit metric sets to access data sources or cubes directly and choose which columns or dimensions to view and analyze, joining data sources together if needed.
- Developers can create and edit data cubes and access the full set of data transformation, querying, and scripting options.
Standard users can interact with metric sets created by other users but not directly with any data sources or data cubes. Similarly, power users can use data cubes created by developers but cannot see or change how the data cube was set up for them.
For more details, see the article on seat types. Administrators can assign seat types on individual user accounts, or to groups of users that use floating seats.
3. Feature security
Application privileges control which users have access to specific capabilities and functionality. For example, users can be prevented from making measure value corrections that will be seen by other users, or writing manual queries that modify data sources. You can also customize the options shown in the UI such as filtering or sharing/exporting. See the article on application privileges for the full list.
Application privileges can be set up by administrators on user accounts or groups of users, or they can be disabled on views or visualizations along with other options such as Re-Visualize menu items for anyone viewing that dashboard, report, or other view.
4. Content security
Each piece of content is saved as a file, including data connectors, data cubes, and dashboards. Each file is located in a project that is set up for personal use, collaboration in teams, or for sharing.
Security privileges can be set up on projects, folders, or individual files to customize which accounts or groups can access them and their level of access. For example, on each item, you can decide who can read (e.g., view), write (e.g., edit), list folder contents, or delete a file. Grouping files into folders allows you to set up security privileges on all contained files together.
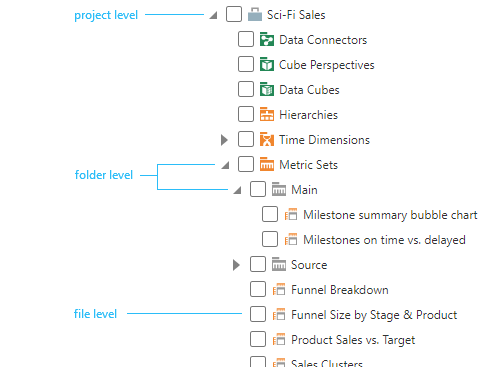
Any user can customize the security privileges on an item if they are assigned the Full Control privilege on it themselves, for example if they created the file. For a full list of security privileges and how to set them, see the article on file and folder properties.
5. Data security
5.1. Row-level security
User-based filtering of data or row-level security is supported using attributes that describe each logged-in user and can be used to filter the data they see. You can create your own custom attributes and assign values to user accounts or groups of users to use for filtering against a particular column, for example returning only data where the Region is North America for the appropriate users.
- Set up a security hierarchy based on custom attributes to completely hide non-applicable values from users, including in filters, while allowing for the option to use data cube storage options.
- You can also configure a transform in a data cube to filter the data according to an attribute such as account name or a custom attribute.
- Some data sources may already have row-level security set up. If you use impersonated Windows credentials or roles impersonation when creating the data connector, or if each user creates their own data connector with their own credentials, each user will see data according to the existing rules.
- Different data can be provided for different tenants using dedicated multi-tenancy features.
5.2. Column-level security
In version 26 and higher, you can set up column security privileges on each output element of a data cube. For the users and groups of users denied access, values will completely or partially masked or removed according to the specified settings.
Table-level and column-level security is also possible by preparing data connectors or data cubes to provide only the tables, columns, or cubes that should be accessible. Select data structures to include under a data connector, or columns to include in a data cube's select transform or process result. When connecting to an OLAP database, cube perspectives define a subset of measures and dimensions to be provided when using them. File security privileges can be used to provide read access to only the appropriate files for each user. DundasScript used for example in a data cube's calculated element can check the current session and the user's attributes or custom attributes to determine which values should be displayed depending on the user.
Metric sets have options to make use of measures for formulas or states, for example, but hide their values completely from users visualizing the result or exporting the data. If users should be able to visualize but not export data, you can also prevent export of metric sets or only certain measures or hierarchies.
6. Organizational security
Your organization's infrastructure and security practices are supported by various features including the following.
6.1. Authentication
Rather than requiring setup of separate accounts and credentials, built-in integration is supported with a variety of identity providers you may already be using at your organization and single sign-on so that users don't need to sign into the application separately.
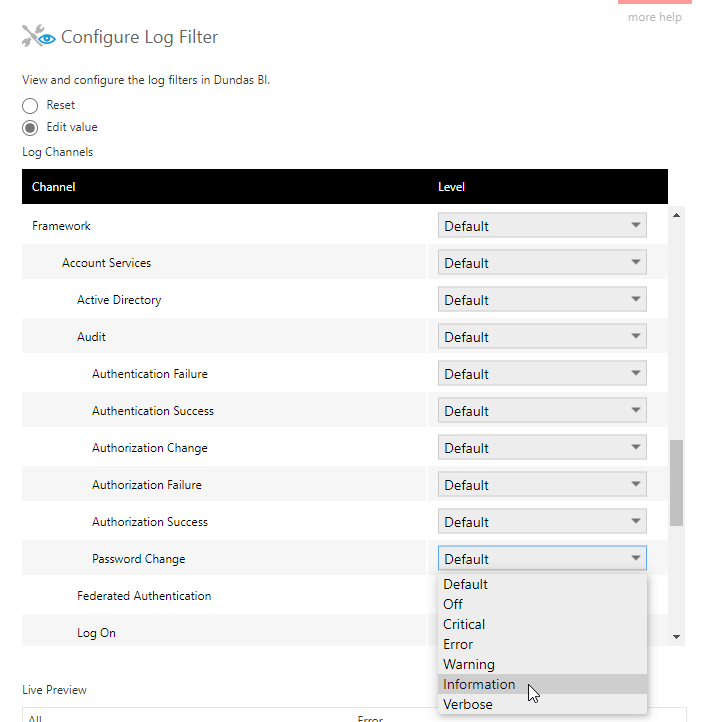
6.2. Auditing
Fine-grained logging options are provided that can be used to keep track of authentication, authorization, and other events in the application logs. Entries are determined by the Log Filter in the configuration settings.
6.3. Usage tracking
Your application instance can locally record usage data, for example which users are viewing which dashboards and reports and for how long. You can then review this data using the Usage Tracking Dashboard sample available from the Deployment application, or you can analyze the data yourself.
6.4. Data privacy
You can choose to install the application on your own IT infrastructure. Within the application, the amount and type of data that you wish to expose to your users is always entirely within your control.
6.5. Multi-tenancy
If you are providing access to the software to different customers or departments, or another scenario requiring isolation between different groups of users, there is built-in dedicated support for separate tenants. Each tenant can operate as if it was its own application with separate licensing, administrators, users, and groups, where tenant users will never know about the existence of other tenants. Tenant users can be allowed to create and manage their own content while allowing you to also share content across all tenants.
At the same time, you have the flexibility of providing shared content to multiple tenants while providing them with only tenant-specific data by using tenant overrides.
For details on tenant management and options, see the article on multi-tenancy.
7. Configuration settings
You can secure the application using many configuration options to meet your own needs, such as:
- IP locks: Administrators can limit access to admin accounts to a range of IP addresses, limit IP addresses/ranges for other accounts and groups (version 8 and above), and lock each logon session to its specific IP address.
- Excessive logon failure protection & password policies: When accounts and credentials are managed within the application, use built-in safeguards against attacks.
- Email whitelists: Prevent users from sharing potentially sensitive content from the application by e-mailing outside of your organization or to non-users.
- Limit data sources: Administrators can limit the data providers that other users can connect to on their own, for example allowing only Excel and flat files and adding trusted connections to databases or prepared data cube models for them to use.
Our configuration best practices guide provides a full list of recommended security configuration settings.
8. See also
- Administration overview
- Accounts
- Groups
- Licensing
- Seat types
- Application privileges
- File and folder properties
- Single sign-on (SSO)
- Multi-tenancy
- Configuration best practices